Part 1 of 3
Scenario: This month presented me with an interesting issue that I would like to share. In effort to provide Role Based Accounts (RBA) to both 1st and 2nd Line Support it became clear that 2nd Line needed to locally administer DCs as they also acted as File Servers at some sites, but being a member of Domain Admins was overkill and as such went against Least Privilege best practices. The solution to this issue was to convert all non-dedicated DCs or FSMO Role holders to Read Only Domain Controllers (RODCs). RODCs run as member servers with a local Security Accounts Manager (SAM) and run AD as an isolated service; this allowed me to configure dedicated local administration. This was achieved by adding the 2nd Line role based account group to the BUILTIN\Administrators group on each local RODC. There are other benefits to RODCs but I’ll not cover those in this post.
Now the issue is that this particular Domain has over 150 DCs that need to be converted to RODCs with the majority being on slow WAN links. I needed to find a way to do this with minimum network traffic, in a consistent manor (to keep the Change Manager happy) and quickly. This was how I did it:
Summary of steps to perform:
1. Sort all Computer and User Objects into Groups that will be used for Password Replication Policies.
2. Set the DNS Server options on each DC NIC to point back to the Core DCs in Head Office.
3. Use the “Install From Media” option of NTDSUTIL to create two local cache copies of the Active Directory. One will be for RODCs and the other will be for Full DCs, the latter could be used for Roll Back scenarios should I wish to restore the DC to its original state.
4. Enable CredSSP used for multihop authentication.
5. Create DCPROMO demote and RODC promote answer files using a word replace template method.
6. DCPROMO demote the DC to a Member Server.
7. Force a restart of the Servers.
8. ReDCPROMO to RODC.
9. Replicate the Passwords for the User and Computer Objects to the local RODC responsible for authentication.
Step 1 – Sort all Computer and User Objects into Groups that will be used for Password Replication Policies
Luckily this step was particularly straight forward for me due to the fact that we use a five letter code for each customer and this code is used to reference the Site, Parent OU and is also used to prefix the Computer Objects. All I needed to do was create an array of all the Site Codes and store it in a variable called $siteCode, then pass that through to a foreach loop that collected all the Computer Objects for that OU and then added them to a Group following a simple pattern match.
This is the code that I used for the first batch of ten (Please note that I used the free Quest AD cmdlets for this and some of the other steps and as such they will need to be installed for this to work):
$siteCodes[0..9] | % {
$siteCode = $($_)
#Sort Computer Membership
$Comps = Get-QADComputer -OU domain1.sch.uk/Schools/$siteCode | ? { $_.memberof.count -ne 1 }
$Comps | ? { $_.Name -match "$($siteCode)W" } | % { Add-QADGroupMember -Identity "$($siteCode)-Workstations" -Member $_.DN }
$Comps | ? { $_.Name -match "$($siteCode)L" } | % { Add-QADGroupMember -Identity "$($siteCode)-Laptops" -Member $_.DN }
}
I also used the below code to list any Computer Objects that were not a member of a single Group, which for me mainly highlighted incorrectly named systems.
$siteCodes[0..9] | % {
$siteCode = $($_)
#Check for Problem Systems
Get-QADComputer -OU domain1.sch.uk/Schools/$siteCode | select name,@{name='MemberShipCount';expression={$_.memberof.count}} | ? { $_.Membershipcount -ne 1 }
}
Step 2 – Set the DNS Server options on each DC NIC to point back to the Full DCs in Head Office.
If you’re going to DCPROMO demote a Server from a DC to a Member Server you will need to be sure that the Server does not reference itself as a DNS Server. I needed to find the teamed NIC that is configured with the DNS registered IP Address of that Server and reconfigure the DNS Search Order. I did this by using PowerShell Remoting to first collect the IP Address from DNS that references the Servers host name and then that information to find the NIC with that configured, and then use a WMI method to set this NICs DNS Search Order to an Array using a couple of DNS Server from Head Office.
#Set DNS
icm $Servers -ScriptBlock { $DNSArray = '10.10.10.10','10.10.10.11' ; (Get-WmiObject -class win32_networkadapterconfiguration | ? { $_.IPAddress -eq ( ([System.Net.Dns]::GetHostEntry($ENV:ComputerName).AddressList | ? { $_.AddressFamily -eq 'InterNetwork' }).IPAddressToString ) } ).SetDNSServerSearchOrder($DNSArray) }
To Check my configuration Changes:
#Audit DNS
icm $Servers -ScriptBlock { Get-WmiObject -class win32_networkadapterconfiguration | ? { $_.IPAddress -eq ( ([System.Net.Dns]::GetHostEntry($ENV:ComputerName).AddressList | ? { $_.AddressFamily -eq 'InterNetwork' }).IPAddressToString )} } | select __SERVER,IPAddress,DNSServerSearchOrder
Step 3 – Use the “Install From Media” (IFM) option of NTDSUTIL to create two local cache copies of the Active Directory.
One will be for RODCs and the other will be for Full DCs, the latter could be used for Roll Back scenarios should I wish to restore the DC to its original state.
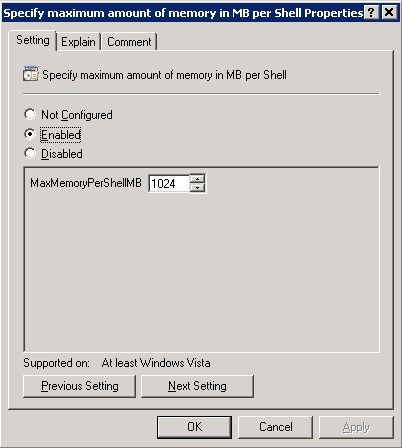
To begin with I needed to increase the amount of memory that a PowerShell remoting session can use from the default 150MB to 1GB due to the memory hungry IFM process. This setting can be restored as soon as you have finished creating your IFM snapshots. Using the Group Policy Management Console (GPMC) I edited the policy that manages Remoting and edited the setting Computer Configuration/Administrative Templates/Windows Components/Windows Remote Shell/ Specify maximum amount of memory in MB per Shell, this option should look like Figure1.
The next step is to create the actual IFM snapshots using NTDSUTIL. This again was achieved using PowerShell Remoting; here is the code I used:
icm $Servers -ScriptBlock { ntdsutil "Activate Instance NTDS" ifm "Create SYSVOL Full C:\Support\IFM_Full" q q >> C:\Support\IFM_Full.log }
icm $Servers -ScriptBlock { ntdsutil "Activate Instance NTDS" ifm "Create SYSVOL RODC C:\Support\IFM_RODC" q q >> C:\Support\IFM_RODC.log }
Thanks for reading. I will post the remaining two parts over the course of the week so please check back.
Regards,
jfrmilner